Finding a Security Bug in My University’s ERP Portal
As a student interested in cybersecurity, I recently discovered a concerning vulnerability in my university’s VTOP portal that handles summer internship project registrations. Here’s what I found and how I responsibly disclosed it.
The Issue
While using the portal, I noticed that the role-based access controls weren’t properly implemented. This meant I could potentially access other students’ internship project details - something that should definitely be private!
Technical Details
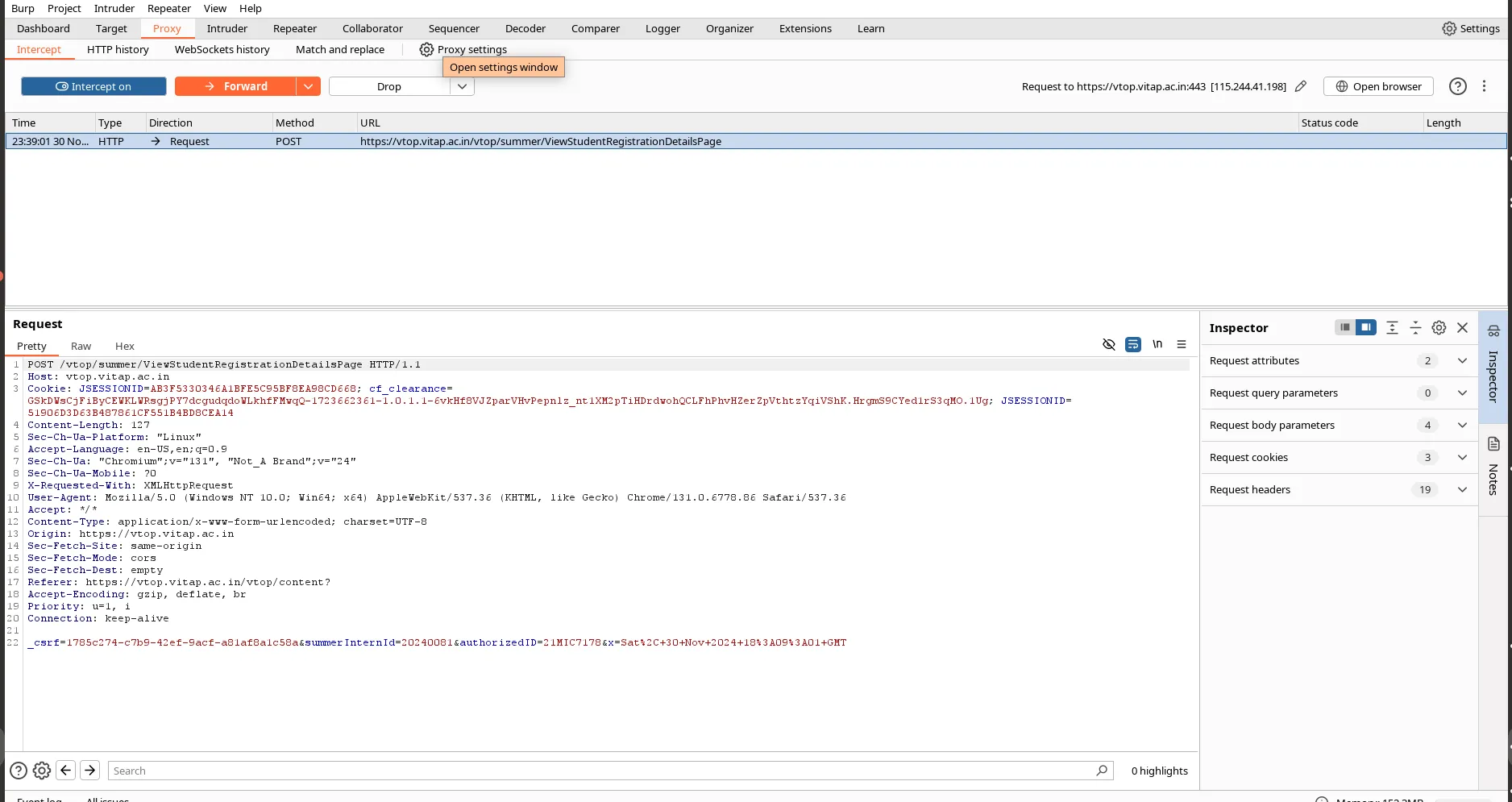
The vulnerability existed in this API endpoint:
POST /vtop/summer/ViewStudentRegistrationDetailsPage HTTP/1.1
Host: vtop.vitap.ac.in
This falls under OWASP’s A01:2021-Broken Access Control category.
How I Found It
Using Burp Suite as my proxy tool, I was able to:
- Intercept the API requests
- Identify the project ID parameter
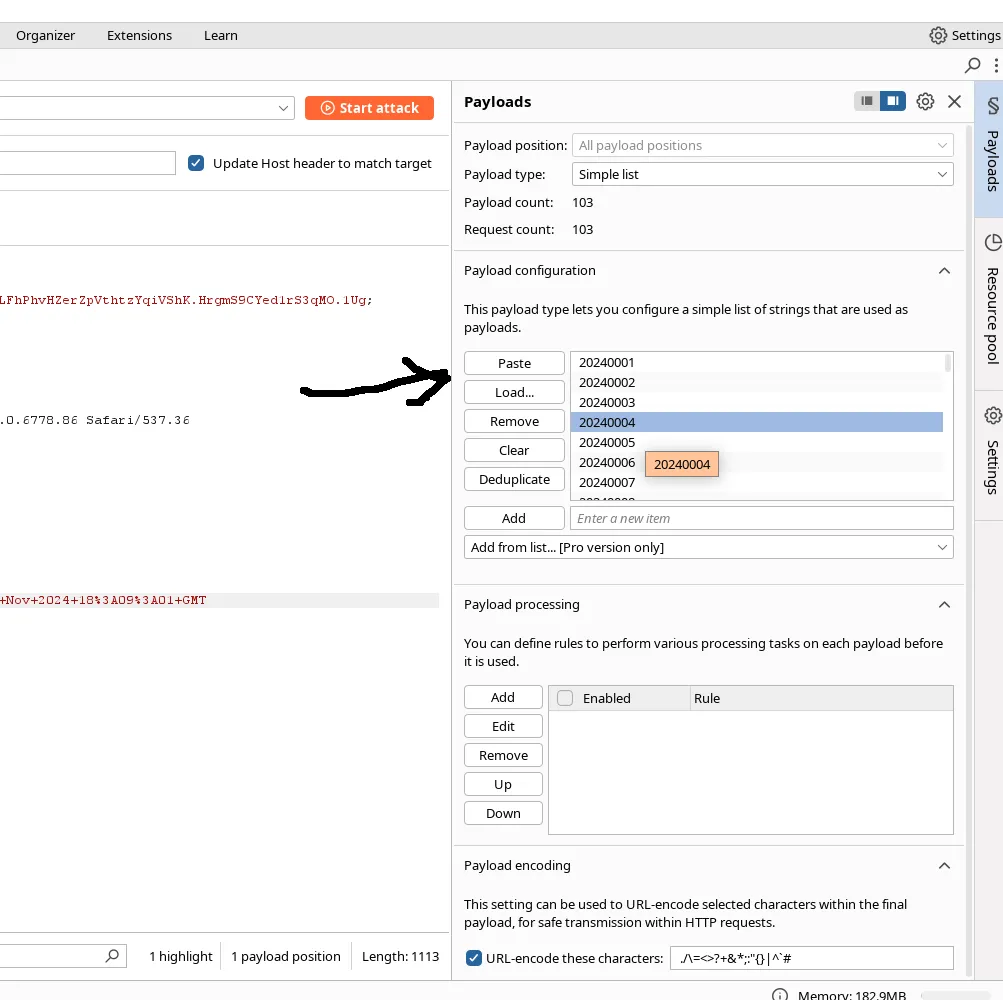
- Test different project IDs using Burp Suite’s Intruder
Here’s what that looked like:
Added the payload dictionary in the Burp Suite Intruder.
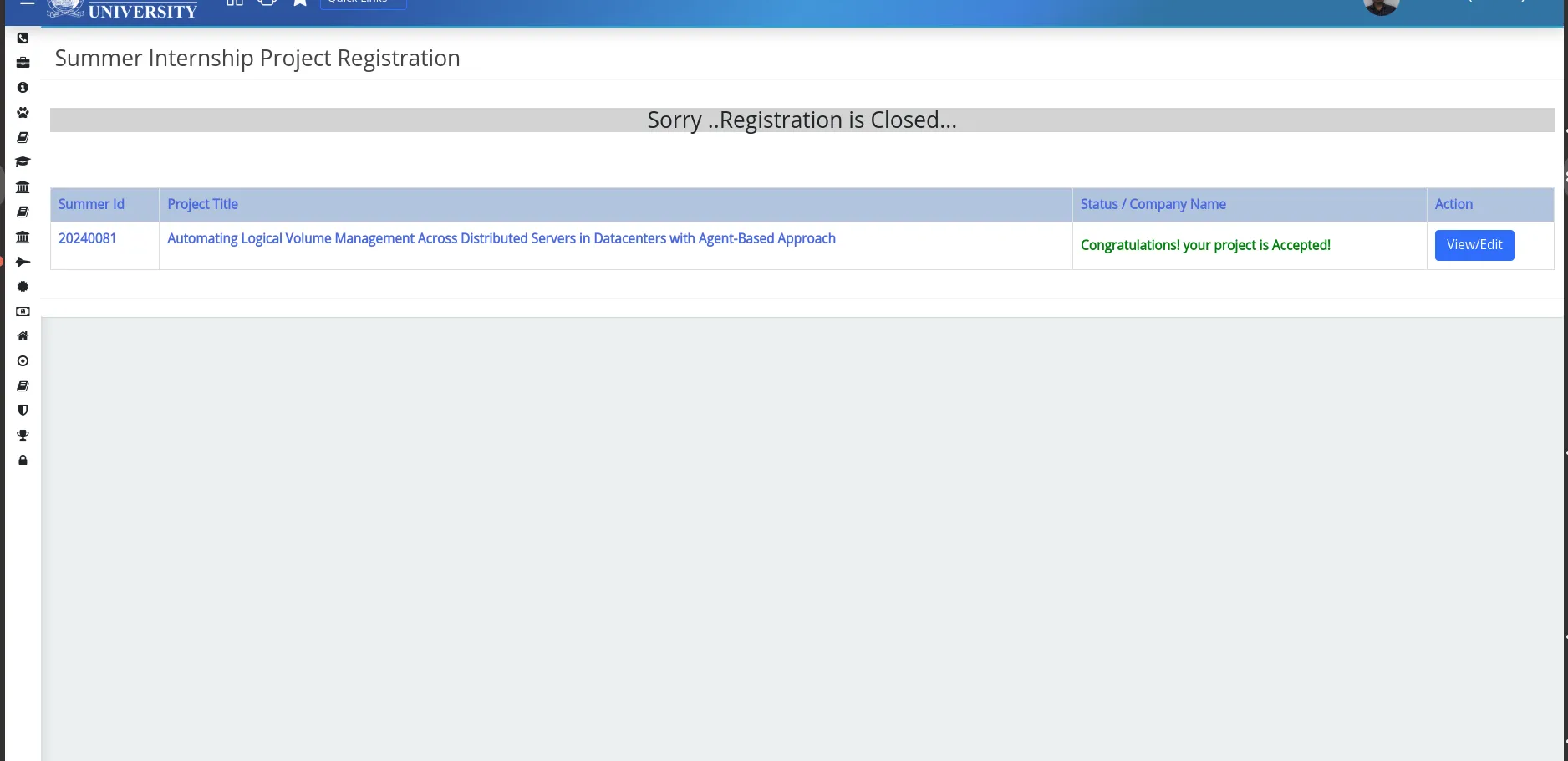
Bruteforcing for API content retrieval of project data, resulting in a misconfigured data leak.
Demo: YouTube Video
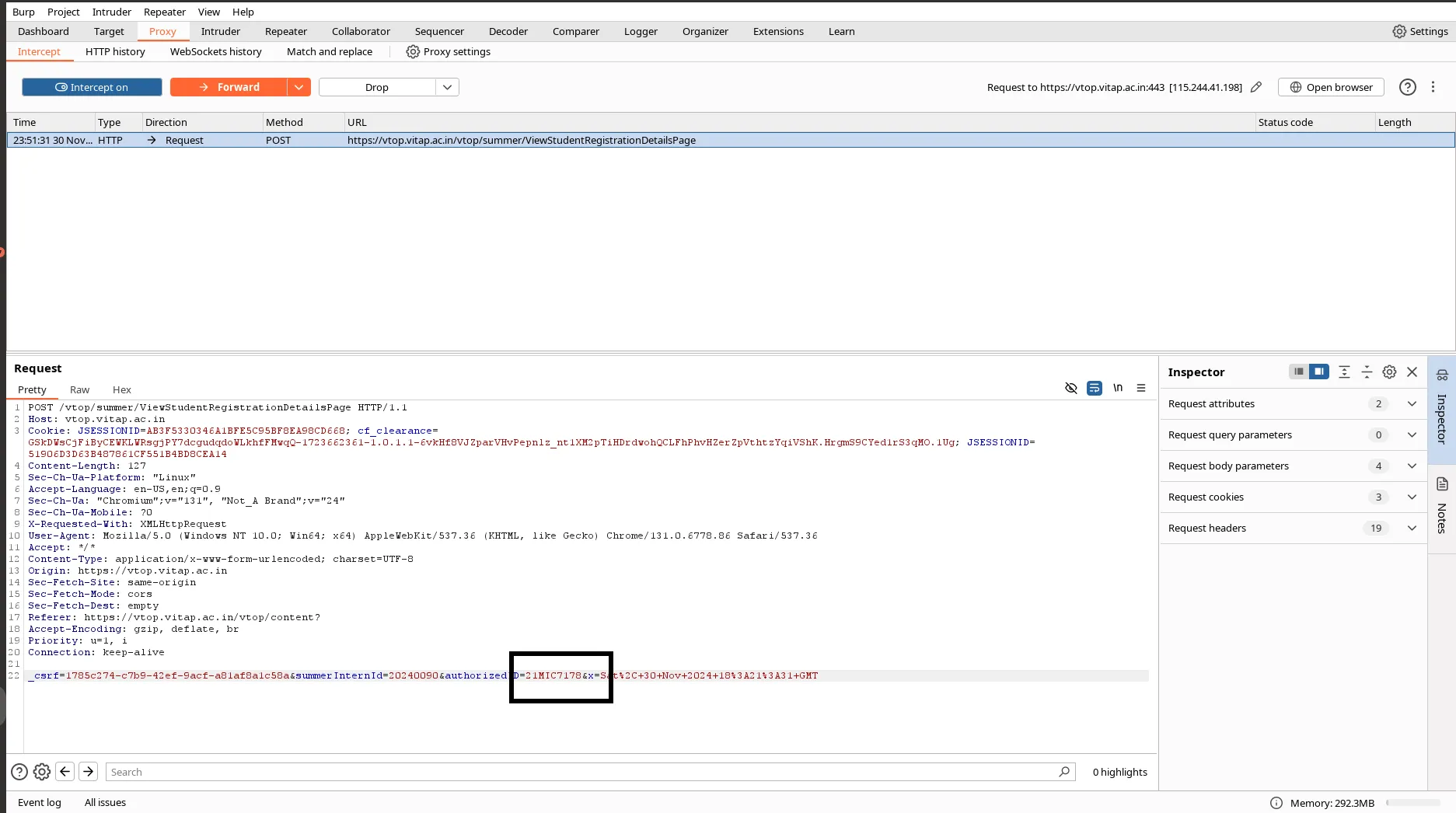
Misconfigured RBAC (Role-Based Access) Behavior:
After intercepting the ViewStudentRegistrationDetailsPage sub API route, changing/replacing it with another existing project ID from the intercepted API body.
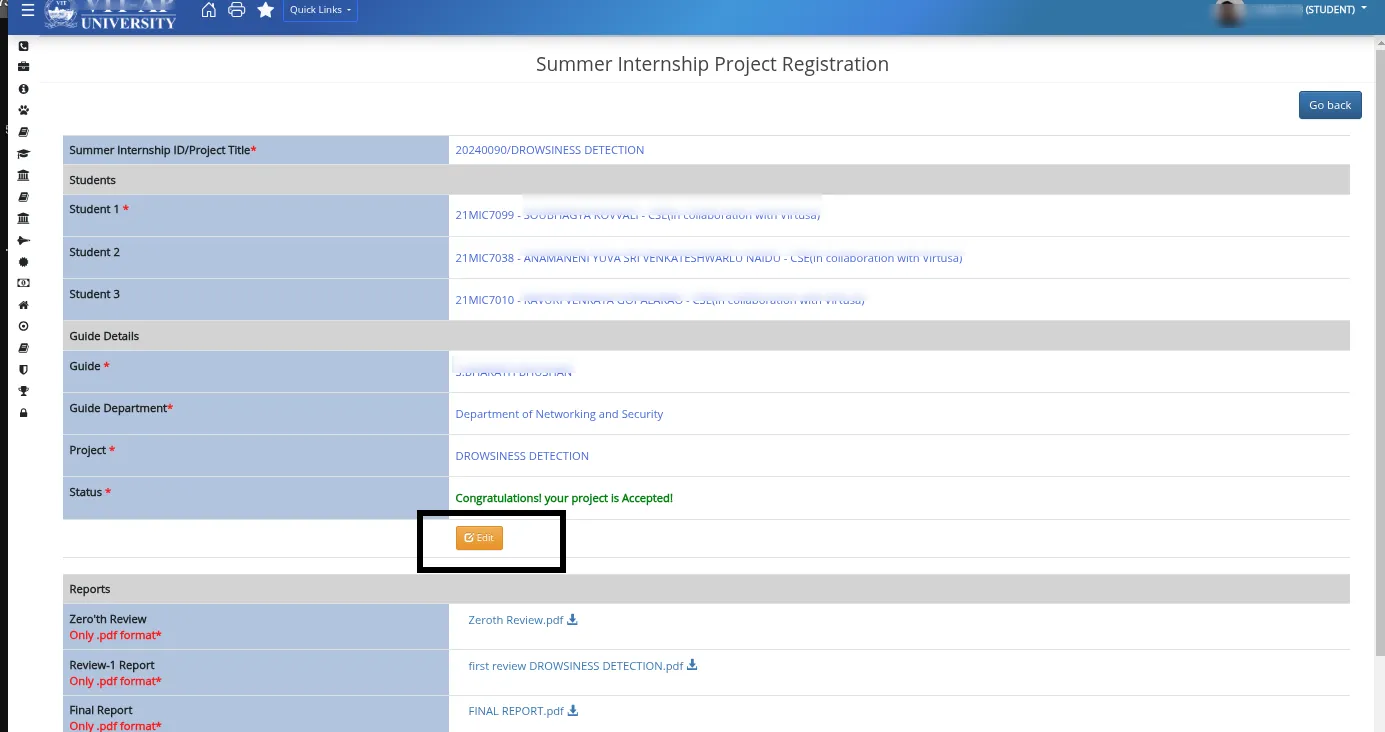
Gained access to files and edit access to others’ forms.
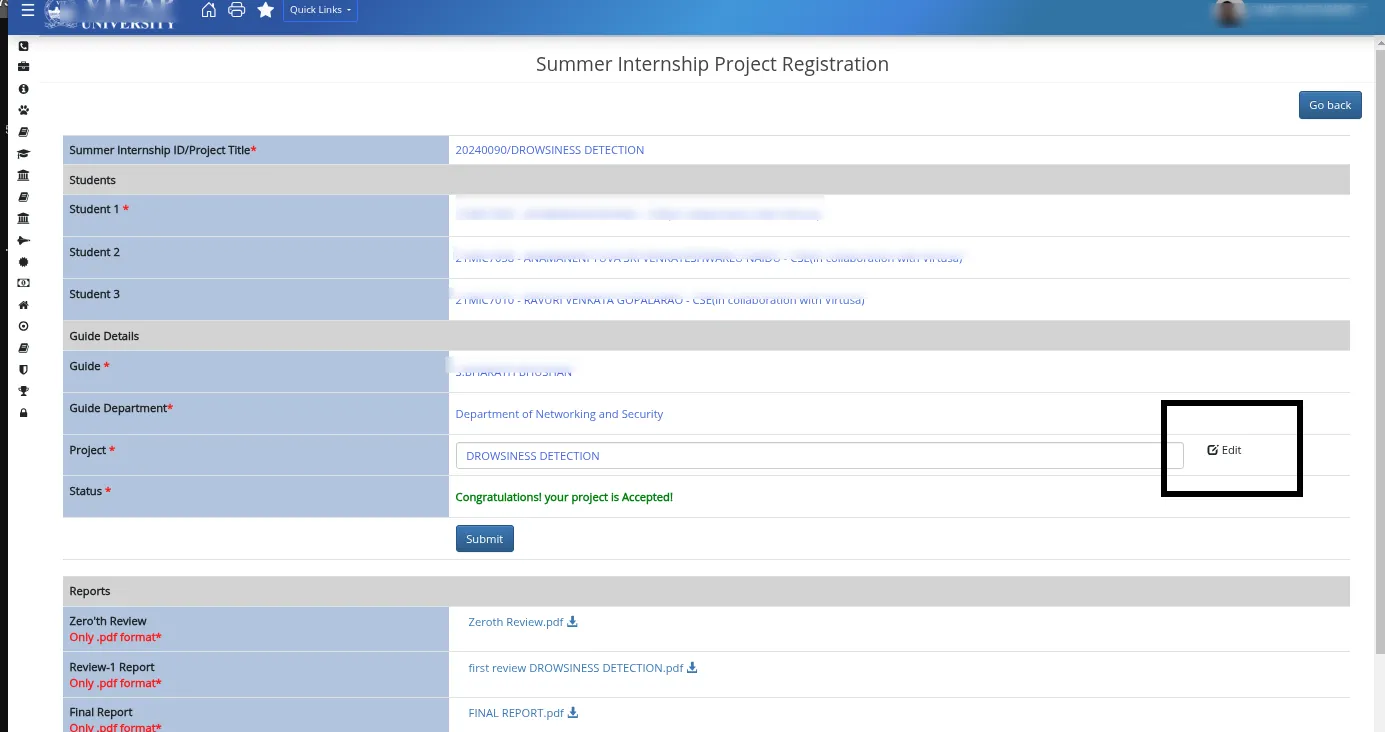
Expected Behavior:
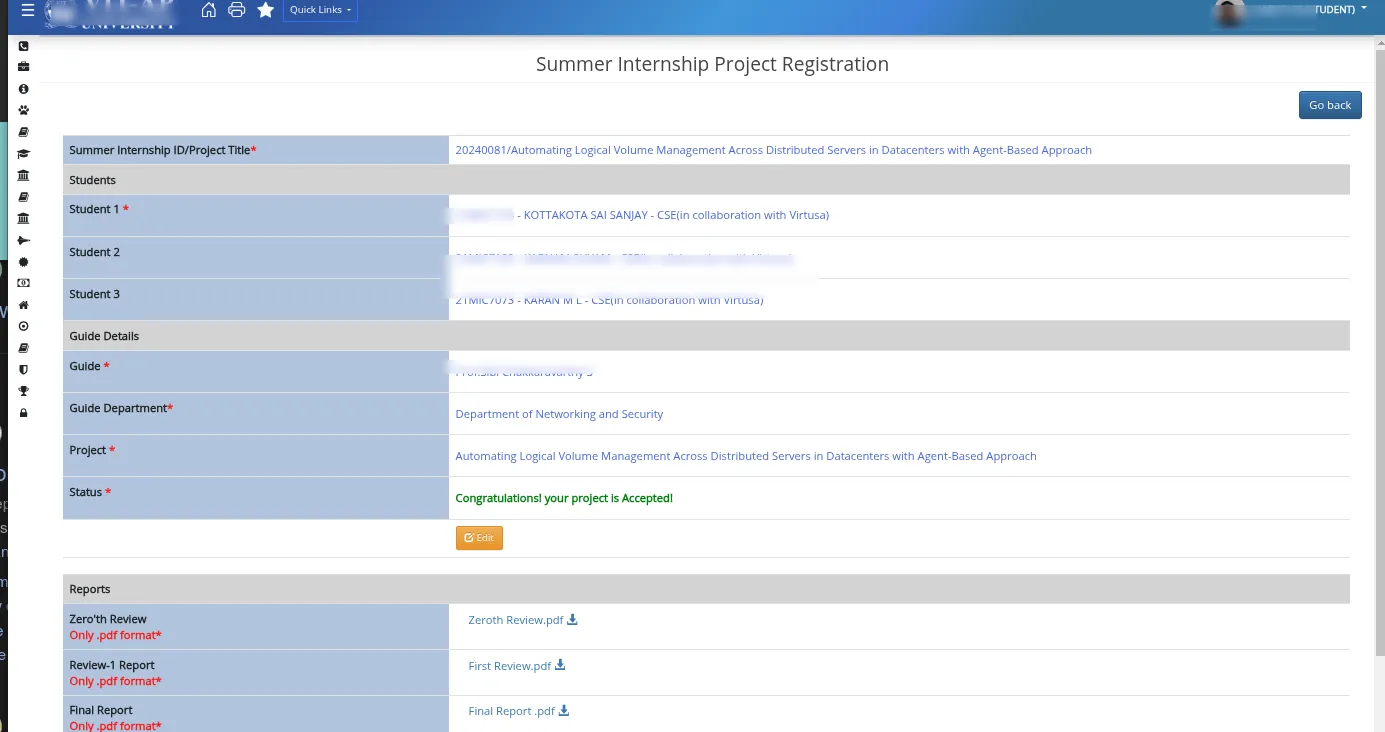
My registration form content, for example: